Threat Analysis
Karakurt vs. Conti Compare and Contrast
As it pertains to cyber insurance and current OFAC sanctions
Executive Summary
With a handful of recent cyber threat intelligence reports alleging direct organizational ties between Conti and Karakurt – some may ask why does it matter if Karakurt is an organizational component of Conti as opposed to an ecosystem affiliate?
Although seemingly simple, this question has significant implications for insurance providers and policyholders alike. Members of Conti are specifically identified as a Russia-aligned OFAC sanctioned entity whereas Karakurt is not, nor are any of its members. It is illegal in the United States to make any payment to Specially Designated Nationals (SDNs) identified to be Conti members whereas Karakurt payments are not contraindicated directly. However, in 2022 Arctic Wolf, ChainAnalysis and Intel471 reporting hypothesized the link between Karakurt as an extension of Conti.
Karakurt’s specialty is data exfiltration and publicly posting or shaming a victim if payment is not made, making it a ‘double extortion’ tactic. This type of attack involving data theft as a component of the operation has increased significantly, now occurring in approximately 70% of negotiated ransomware cases, up from ~40% in mid-2021. In this article we outline the implications of double extortion tactics and of the current affiliate ecosystem for insurers and insured alike.
Karakurt Group Lineage
Before diving into the technical reasons for this hypothesis, let’s start with a brief overview of the Karakurt group itself. The name’s origin can be traced back to one of the world’s most dangerous spiders known to live specifically in Russia’s Astrakhan region, as well as other parts of eastern Europe and Siberia.

Graphic 1: Karakurt Ransomware
Group Logo

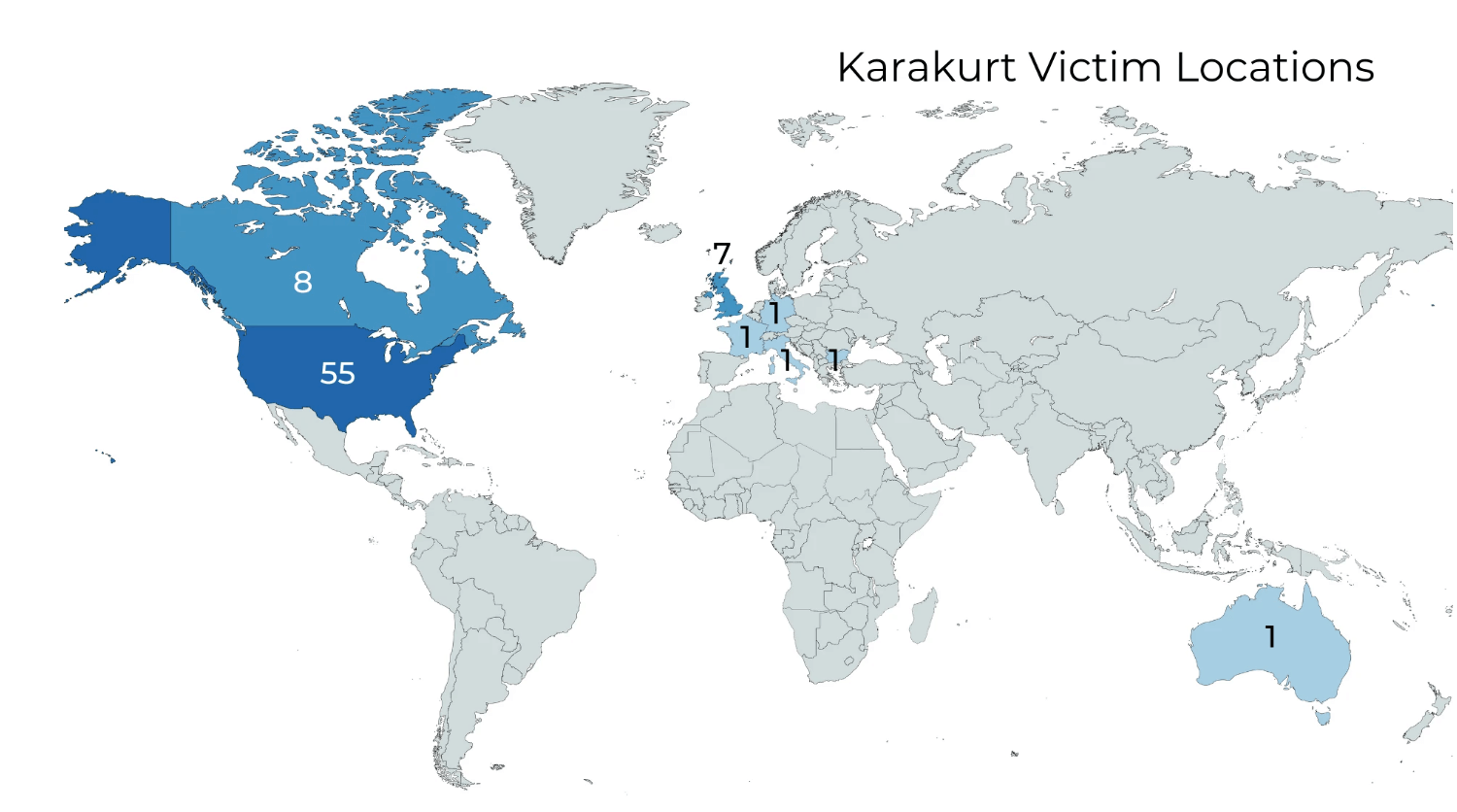
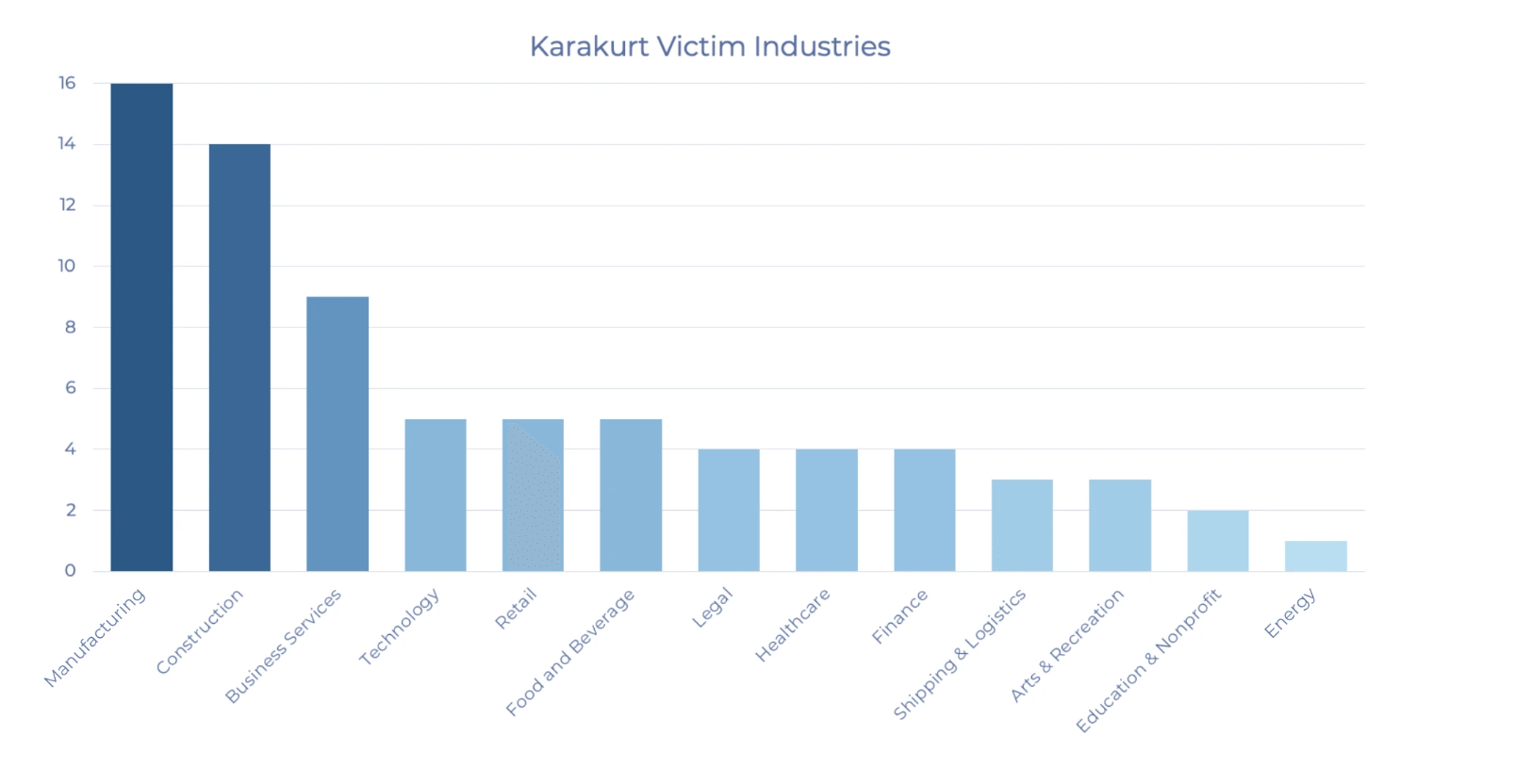
As previously stated, Karakurt’s specialty is data exfiltration and extortion as opposed to the more typical mass-encryption-style ransomware attacks. While specific TTPs are outlined below in the Connected Hypothesis section, it’s worth noting that this group is adept at leveraging native tools and favors a “Living-off-the-land” (LotL) approach for post-exploitation as opposed to the commonly observed and typically monitored for Cobalt Strike. Karakurt targets large organizations with revenue to support higher ransom demands, typically ranging from US $25,000 to US $13 million in cryptocurrency.
As a final point to consider prior to paying any ransom (as it pertains to Conti with secondary attacks attributed to Karakurt), ~80% of victims who also paid a ransom to restore systems were attacked again.
Reasons for the Connected Hypothesis
The idea that Conti and Karakurt are formally connected in some capacity began when Accenture discovered a Conti-planted-backdoor being leveraged for a secondary attack by Karakurt. This initial observation was further strengthened by Arctic Wolf’s Tetra Defense group hypothesis that such access could only have been gained via some type of organized purchase, pre-established operational relationship, or by some type of Karakurt compromise of pre-established Conti infrastructure. An additional point of similar behavior came in the form of a leave-behind file labeled “file-tree.txt” in the victim’s environment, as well as the initial points of intrusion (including the use of Fortinet SSL VPNs). The last nail in the proverbial coffin came when Chainanalysis identified dozens of cryptocurrency wallets belonging to Karakurt that were transferring significant funds to Conti-owned wallets. In the same analysis, security researchers also discovered a shared wallet hosting both Conti and Karakurt victim payment addresses leaving little doubt that both were deployed by the same affiliate.
DISCLAIMER:
The reporting contained herein from the Nisos research organization consists of analysis reflecting assessments of probability and levels of confidence and should not necessarily be construed as fact. All content is provided on an as-is basis and does not constitute professional advice, and its accuracy reflects the reliability, timeliness, authority, and relevancy of the sourcing underlying those analytic assessments.
About Nisos®
Nisos is The Managed Intelligence Company®. Our analyst-led intel investigations, assessments, and monitoring services empower your security, intelligence and trust and safety teams. We provide accurate, customized intelligence that guides your security and risk decisions – protecting your organization, assets, and people. Learn more at nisos.com.
