Blog
Trigona Ransomware Family Explained
Executive Summary
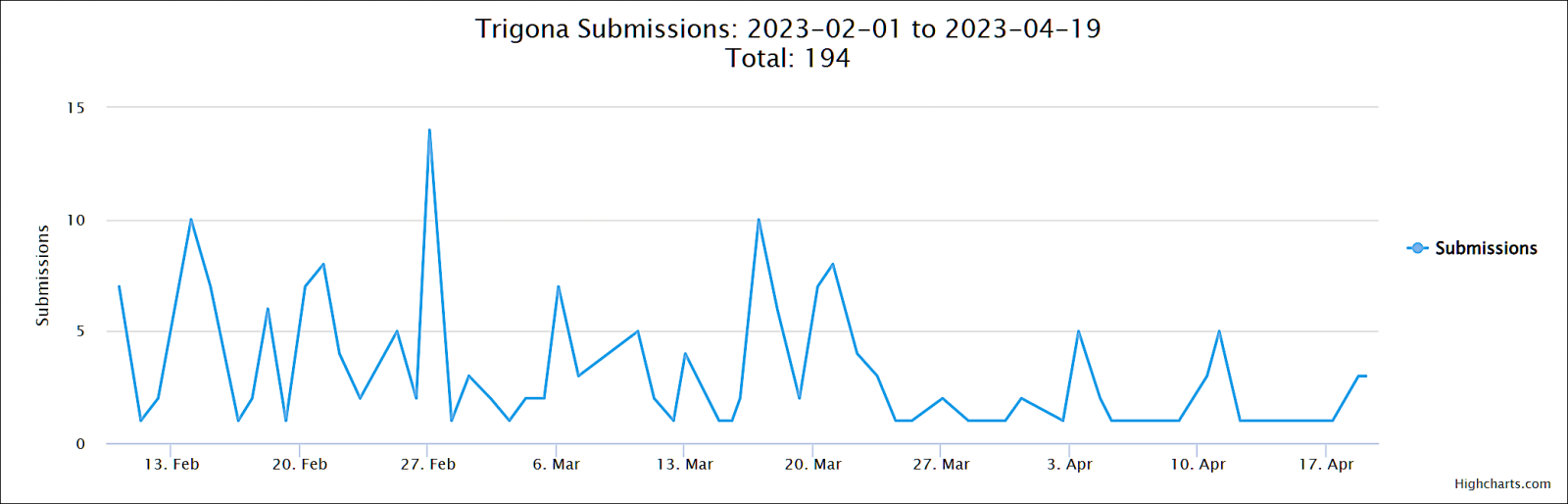
Although not officially branded as ‘Trigona’ until October 2022, samples of the ransomware strain have been observed globally prior to the re-branding due to Trigona’s unique characteristics. First, Trigona is written in Delphi programming language, enabling the ransomware to leverage password-protected executables in order to obfuscate the malicious content within. (See source 1 in appendix) Additionally, the ransomware group utilizes an HTML application as a substitute for the typical text-file-based ransomware note. (See source 2 in appendix) As of February 2023 there have been at least 17 possible Trigona victims identified in the U.S., France, Italy, Germany, Australia and New Zealand. (See source 3 and 4 in appendix) The ransomware operators appear to be primarily targeting marketing and finance organizations but the construction, agriculture, and high technology market segments are also impacted. (See source 5 in appendix)
Source: BleepingComputer
Source: BleepingComputer (See source 7 in appendix)
Etymology and Group Lineage
Trigona shares commonalities with ALPHV/BlackCat and Crylock in terms of actual payload and typical operating norms. Similar to ALPHV/BlackCat, Trigona has been observed exploiting a Zoho ManageEngine ADSelfService Plus vulnerability and follows common living-off-the-land (LotL) tactics by leveraging legitimate tools already present in the victim’s environment. More directly, Trigona leverages ALPHV/BlackCat’s reputation and data leak site as an additional payment pressuring tactic. (See source 8 in appendix)
Another functional similarity between the two ransomware families is the presence of a data wiper feature. Trigona released the data wiper feature during an update, (see source 9 in appendix) confirmed via VirusTotal, (see source 10 in appendix) around March 12th, 2023 (date identified via SHA hash listed in zscaler wiper-related writeup). (See source 11 in appendix) Despite this similarity, a key distinction between ALPHV/BlackCat and Trigona is the programming language used for the payloads. Trigona’s core payload is built using the Delphi programming language whereas ALPHV/BlackCat’s payload is written in Rust. (See source 12 in appendix)
Trigona also appears to share some characteristics with the CryLock ransomware strain. (See source 13 in appendix) Both ransomware families deliver ransom notes in HTML format and share common language in the notes themselves which contain specific messaging, such as “the price depends on how soon you will contact us.” (See source 14 in appendix) Additionally, both strains leverage RSA and AES encryption with Trigona choosing 4,112-bit RSA and 256-bit AES encryption in Output Feedback Mode (OFM) specifically. (See source 15 in appendix)
High Level Attack Overview
Although the means of initial access remain unconfirmed as early reports vary, unpatched system exploitation and email-based social engineering are the prime suspects. Externally-facing, mismanaged MS-SQL Servers are known to be prime targets for brute-forcing in combination with CLR Shell work. (See source 16 in appendix) Additionally, a specific vulnerability this group exploits is CVE-2021-40539, commonly known as “Zoho ManageEngine ADSelfService Plus authentication bypass”, which is associated with the Rest API’s and ADSelfServices build 6113 and older. (See source 17 in appendix) This exploit allows remote code execution without any required user activity.
Once initial access is gained, Trigona operators upload a file, DC2.exe, (see source 18 in appendix) which will contain the password protected version of the Mimikatz executable. By being password protected, the executable’s true purpose is obfuscated from most common detection mechanisms making the credential stealing capability fly in under the radar. Mimikatz is then leveraged to either modify existing account credentials, create new accounts, or change user group associations. (See source 19 in appendix)
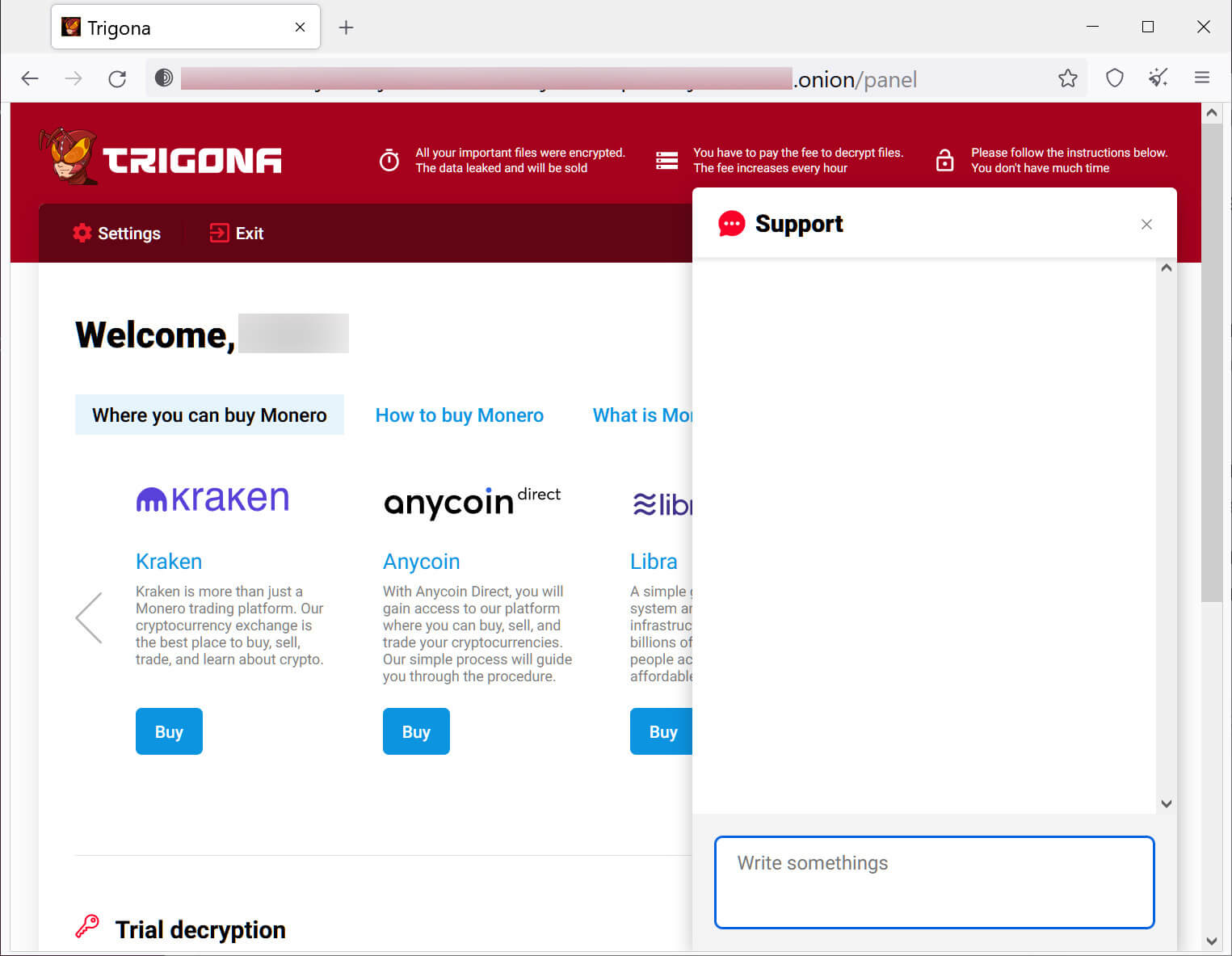
Persistence is established via Registry Run keys with lateraling typically taking place via SMB. Post infection, Trigona-encrypted files get a “._locked” appended to the end of the prior filename. Once file encryption has begun, the group’s ransomware note, “how_to_decrypt.hta”, gets loaded as an HTML application. The ransom note offers free decryption of three (3) victim files and displays the ransomware price which is cited to increase every hour.
Beyond the novelty of using an HTML application as the ransomware note, Trigona operators embed JavaScript that contains unique computer IDs (CIDs) & victim IDs (VIDs) and ask victims to pay with Monero (XMR), a cryptocurrency known for protecting user anonymity, via a dedicated TOR-based payment portal as seen below (Figure 3): (See source 20 in appendix)
Source: BleepingComputer (see source 21 in appendix)
Known Infrastructure & Associated Indicators Of Compromise (IOCs):
MD5 hashes (see source 22 in appendix):
- 1cece45e368656d322b68467ad1b8c02 – Trigona Dropper (svcservice.exe)
- 1e71a0bb69803a2ca902397e08269302 – Batch Runner (svchost.bat)
- 46b639d59fea86c21e5c4b05b3e29617 -CLR SqlShell
- 530967fb3b7d9427552e4ac181a37b9a – Trigona Ransomware (svchost.exe)
- 5db23a2c723cbceabec8d5e545302dc4 – nt.exe
SHA256 hashes (see source 23 in appendix):
- 248e7d2463bbfee6e3141b7e55fa87d73eba50a7daa25bed40a03ee82e93d7db
- 596cf4cc2bbe87d5f19cca11561a93785b6f0e8fa51989bf7db7619582f25864
- 704f1655ce9127d7aab6d82660b48a127b5f00cadd7282acb03c440f21dae5e2
- 859e62c87826a759dbff2594927ead2b5fd23031b37b53233062f68549222311
- 8f8d01131ef7a66fd220dc91388e3c21988d975d54b6e69befd06ad7de9f6079
- 97c79199c2f3f2edf2fdc8c59c8770e1cb8726e7e441da2c4162470a710b35f5
- A86ed15ca8d1da51ca14e55d12b4965fb352b80e75d064df9413954f4e1be0a7
- Accd5bcf57e8f9ef803079396f525955d2cfffbf5fe8279f744ee17a7c7b9aac
- Da32b322268455757a4ef22bdeb009c58eaca9717113f1597675c50e6a36960a
- E7c9ec3048d3ea5b16dce31ec01fd0f1a965f5ae1cbc1276d35e224831d307fc
- E97de28072dd10cde0e778604762aa26ebcb4cef505000d95b4fb95872ad741b
- F29b948905449f330d2e5070d767d0dac4837d0b566eee28282dc78749083684
- Fa6f869798d289ee7b70d00a649145b01a93f425257c05394663ff48c7877b0d
- Fbba6f4fd457dec3e85be2a628e31378dc8d395ae8a927b2dde40880701879f2
- Fd25d5aca273485dec73260bdee67e5ff876eaa687b157250dfa792892f6a1b6
128.90.173.138
128.90.173.148
213.32.39.46
213.32.39.42
213.32.39.38
213.32.39.34
213.32.39.45
213.32.39.43
213.32.39.39
213.32.39.32
213.32.39.41
213.32.39.37
213.32.39.47
213.32.39.36
213.32.39.33
77.73.133.84 (suspected Cobalt Strike C2 server)
168.100.8.135
45.61.137.31
174.138.8.184
194.147.115.40
128.90.170.115
13.125.150.170
206.189.238.130
64.52.80.253
64.190.113.69
23.225.195.56
172.247.15.222
23.225.195.44
172.86.120.248
23.225.195.20
147.75.62.148
172.105.110.202
147.182.145.37
193.149.185.117
157.230.249.23
Onion address of the threat subject: hxxp://3x55o3u2b7cjs54eifja5m3ottxntlubhjzt6k6htp5nrocjmsxxh7ad[.]onion/ (see source 24 in appendix)
Leak site attributed to Trigona: 45.227.253[.]99 (see source 25 in appendix)
Other Trigona Infrastructure identified: 45.227.253[.]106, 45.227.253[.]98. 45.227.253[.]107 (see source 26 in appendix)
The reporting contained herein from the Nisos research organization consists of analysis reflecting assessments of probability and levels of confidence and should not necessarily be construed as fact. All content is provided on an as-is basis and does not constitute professional advice, and its accuracy reflects the reliability, timeliness, authority, and relevancy of the sourcing underlying those analytic assessments.
About Nisos®
Nisos is The Managed Intelligence Company®. Our analyst-led intel investigations, assessments, and monitoring services empower your security, intelligence and trust and safety teams. We provide accurate, customized intelligence that guides your security and risk decisions – protecting your organization, assets, and people. Learn more at nisos.com.