Blog
What Are Bots and How Are They Used?
A bot is a software application that is programmed to do certain tasks. Bots are automated, which means they run according to their instructions without a human user needing to manually start them up every time. Bots often imitate or replace a human user’s behavior and typically do repetitive tasks faster than a human could.
More than half of internet traffic is bots scanning content, interacting with web pages, chatting with users, or looking for attack targets. Some bots are designed with useful, benevolent intentions , such as search engine bots that index content for search, or customer service bots that help users by providing answers to pre-established questions.
Other bots are designed with malice and are programmed to break into user accounts, scan the web for contact information for sending spam, or perform other malicious activities such as creating fake social media accounts.
If it’s connected to the internet, a bot will have an associated IP address and have infrastructure that can be monitored, tracked, reverse engineered, and attributed.
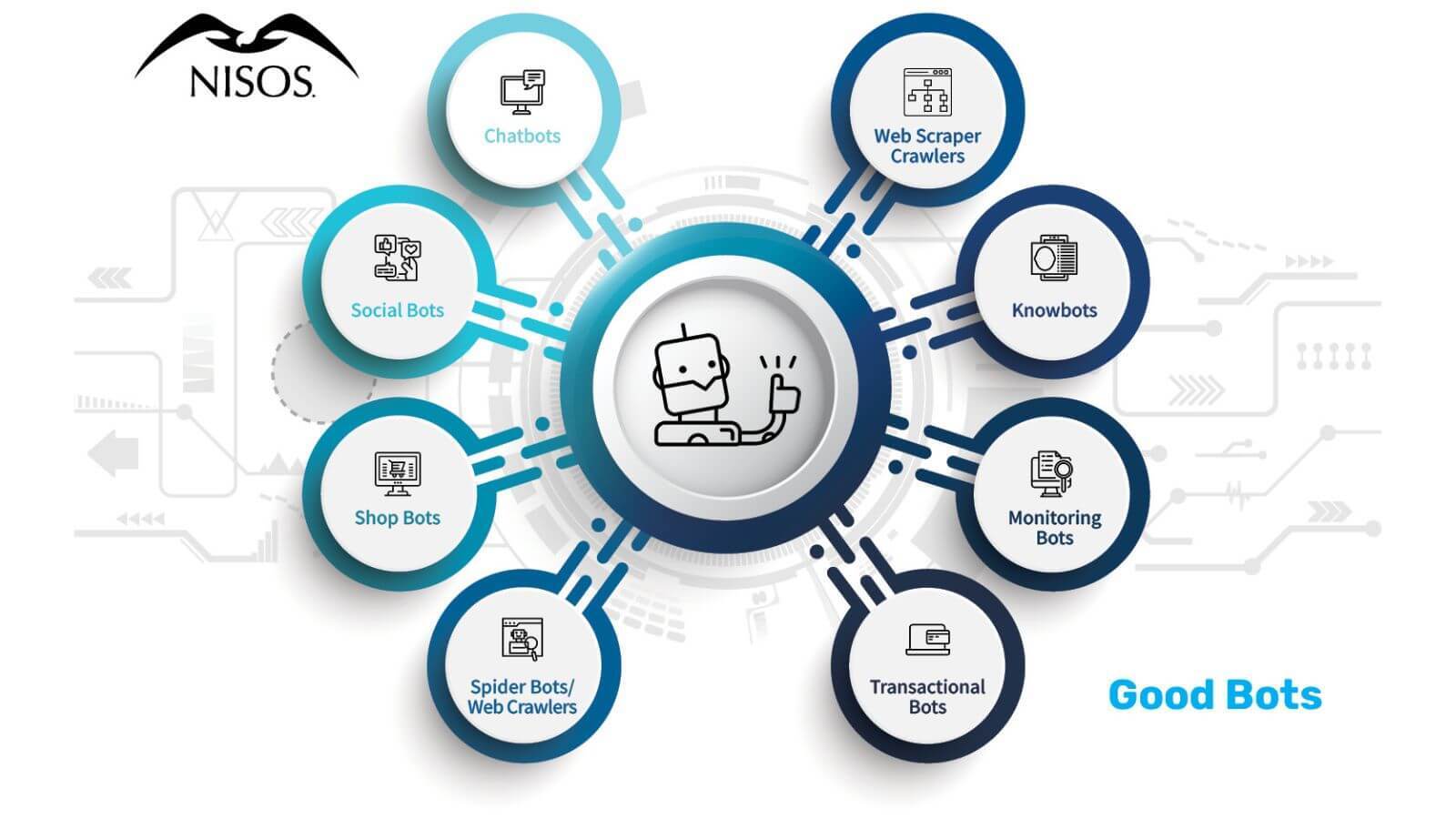
What are Types of Good Bots?
- Chatbots: Bots that simulate a real human interaction using a phrase bank of pre-established phrases.
- Social bots: Bots on social platforms to automatically generate messages, advocate for ideas, or act as a follower of users.
- Shop bots: Bots that browse online to identify deals, coupons, and sales. Some sophisticated bots will track a user’s surfing patterns then modify the content on that site for the user to secure a purchase.
- Spider bots or web crawlers: Bots that scan content on webpages on the internet to help Google and other search engines understand how to answer users’ search queries. Spiders download HTML and other resources, such as CSS, JavaScript, and images, and use them to process site content.
- Web scraper crawlers: Bots that pull, or scrape, data from websites for offline use and reuse. They may select the entire contents of site or only select information. While some scraping is legitimate and may be allowed by website owners, other web owners may deem this activity to be a violation of their terms of use or downright theft or plagiarism.
- Knowbots: Bots that collect information for users by automatically visiting websites to retrieve data.
- Monitoring bots: Bots that monitor the health of a website or system.
- Transactional bots: Bots that complete transactions on behalf of humans.
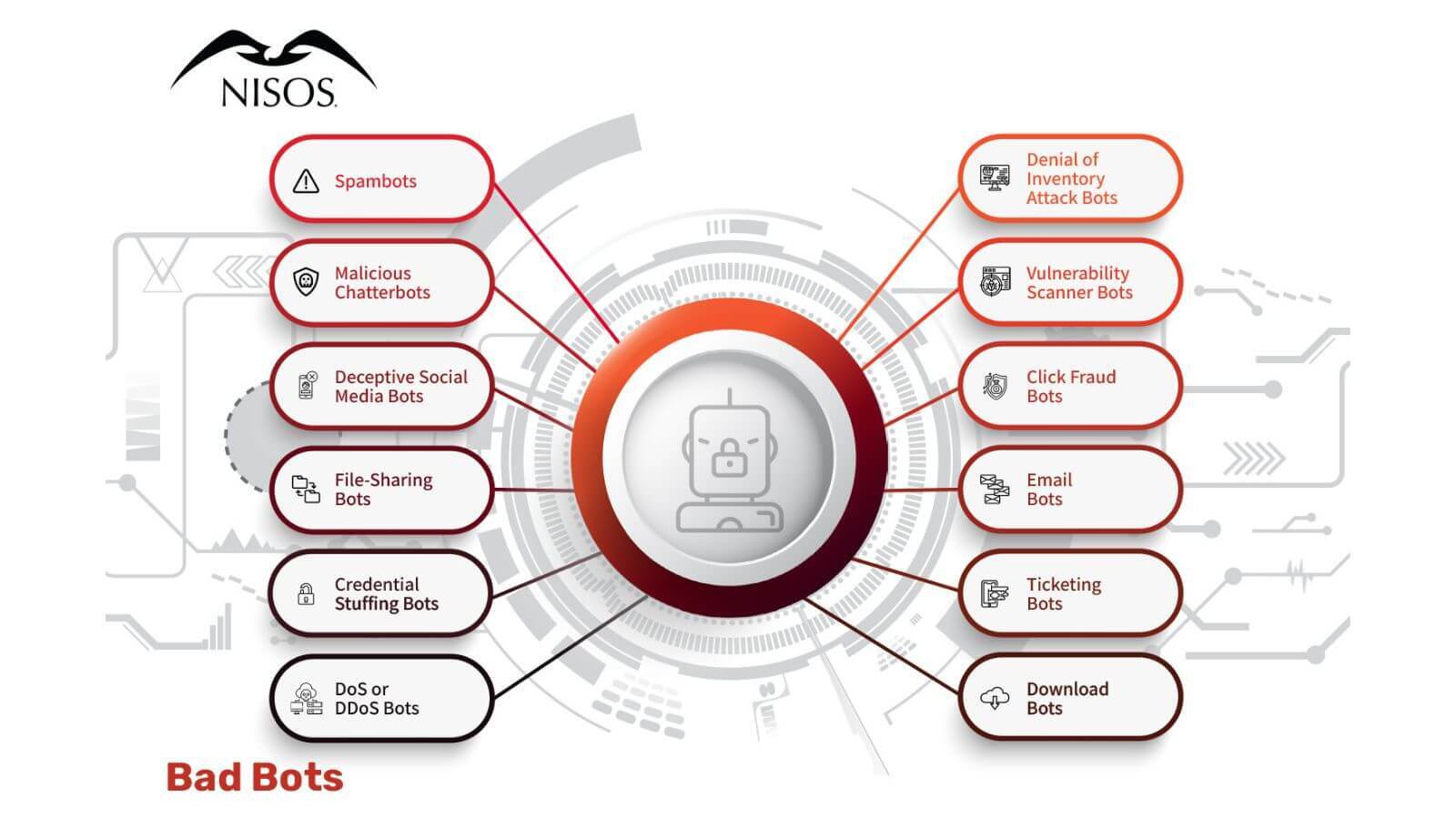
What are Bad or Malicious Bots?
- Spambots: Spambots collect email addresses from website pages. They may also work to promote content in forums or comment sections of communities to drive traffic to specific websites.
- Malicious chatterbots: Dating service websites and apps are havens for malicious chatterbots. These chatterbots pretend to be a person, emulating human interaction, often fooling people who don’t realize they are chatting to harmful programs that may steal personally identifiable information (PII).
- Deceptive social media bots: These bots are used to spread disinformation or promote a particular narrative. They are sometimes used by unscrupulous businesses to falsely promote their products as well as by governments to amplify social narratives.
- File-sharing bots: These bots respond to searcher queries, offering files for download. Of course, when the user clicks the file, they’re usually infecting their computer with viruses and malware.
- Credential stuffing bots: These bots use stolen usernames and passwords to “stuff” forms and gain unauthorized access to online accounts.
- DoS or DDoS bots: This occurs when excessive bot traffic is weaponized by overwhelming or flooding a server. It is often coupled with IoT and router infrastructure takeovers.
- Denial of inventory attack bots: These bots attack shops by listing their products as “not available” or “sold out.” By using the shopping cart, the bots select items, add them to cart, but never complete a transaction. This means that when a real shopper wants to purchase the product, they can’t.
- Vulnerability scanner bots: Bots that report site vulnerabilities for the purpose of notifying bad actors who can sell the information about the vulnerabilities or use it themselves to hack a website.
- Click fraud bots: Very damaging and costly, these bots target advertisers who are paying for digital ads. They defraud marketers by fraudulently clicking on paid ads. Disguised as legitimate traffic, these bots cost advertisers billions of dollars annually.
- Email bots: An email bot is an automated marketing tool that can respond quickly to incoming email leads oftentimes without the user’s permission.
- Ticketing bots: Bots that automate rapidly buying tickets to popular shows and events so they may be scalped later for profit. While this is illegal in many countries, it is universally upsetting to real fans and ticket buyers.
- Download bots: Bots that inflate download statistics by automatically downloading select software or applications. Outside of vanity metrics, they can also be leveraged to attack download sites by creating fake downloads as part of a Denial of Service (DoS) attack.
How to Protect Yourself from Bots
When it comes to “bots” (short for robots) – there are lots of ways they can help and hurt users. Cybercriminals will use bots to steal PII, scam users, and trick people into paying them. They may create DoS or DDoS attacks to slow or disable legitimate websites.
If a business is considering adding a bot, they may see the benefit of eliminating human error and cost for time spent on repetitive tasks. They are available around the clock and can be programmed to stay on message. In the best cases, they improve customer experience and can help improve operational bottlenecks.
But not all bots are helpful. In fact, ineffective bots can create negative customer sentiment by providing a false sense of “support” when they misunderstand a user’s needs or are unable to complete a task or are prohibiting a human from accessing another human to solve their problem.
It’s also important to consider how bots can be programmed with bias or with overt malicious intent. We experience many bot interactions as users. From helper tools in Slack to virtual assistants like Siri and Alexa. But, as you can see, there are more bad bots than good. If you suspect that your computer may be part of a botnet, you may be experiencing anomalous activities like your computer crashing without reason, slow internet, off-line pop ups, and more.
Prevention is important and you can follow good cyber hygiene to avoid most of these issues. The old rules still apply:
- Use anti-malware software and let them auto-update
- Allow software programs to auto-update
- Use a password manager tool to employ strong passwords
- Surf safely – don’t visit sites or click links that looks suspicious
- Install a firewall
Learn More About Bots
Check out:
- Good and Bad Bot Infographic
- Fronton: A Botnet for Creation, Command, and Control
- Colombian Election Disinformation Campaign: The Role of Venezuelan Leftists
- Weaponization for Disinformation – Nisos
- EP3: Know Your Adversary™ – The World of Online Platform Abuse and Fraud
About Nisos®
Nisos is The Managed Intelligence Company®. Our services enable security, intelligence, and trust and safety teams to leverage a world-class intelligence capability tailored to their needs. We fuse robust data collection with a deep understanding of the adversarial mindset delivering smarter defense and more effective response against advanced cyber attacks, disinformation, and abuse of digital platforms.
